The event is arguably the most significant cyber-catastrophe to date and clearly demonstrates the systemic nature of cyber risk. A single vulnerability was utilized to spread malware to over 300,000 machines in over 150 countries causing havoc to industries as diverse as hospitals and car manufacturers.
The cyber extortion campaign we saw on Friday May 12, whilst unprecedented in its spread, was not unexpected. As part of its Cyber Accumulation Management System, RMS models this type of campaign as just one of numerous extreme but plausible cyber-catastrophes that could occur. Over the coming days, RMS will continue to monitor the situation and provide updates to clients to assist in calculating the potential impact of this event.
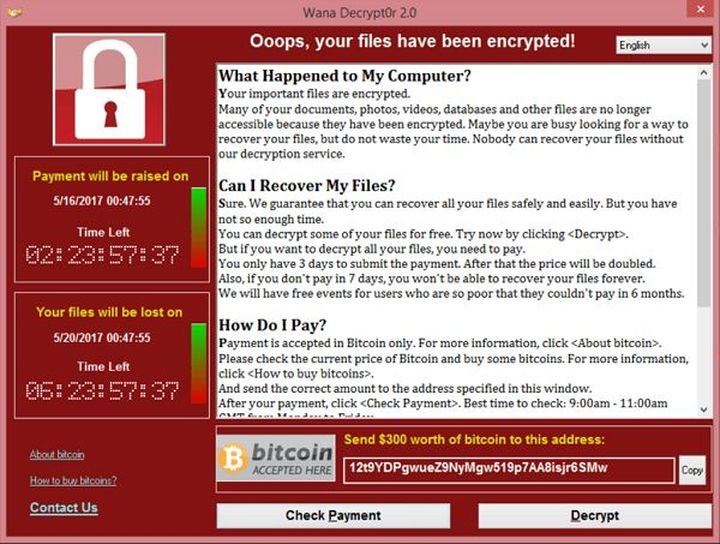
What We Know So Far
In terms of significant malware, WannaCry has reached the same notoriety as the “MyDoom” and “ILOVEYOU” worms and viruses of history.
A ransomware strain named WannaCry started infecting machines globally on Friday May 12. WannaCry uses standard malware infection techniques of a malicious email attachment to infect Windows machines and encrypt all files on the system. A message notifies the user and offers an encryption key in return for a ransom to be paid in Bitcoin. A seven-day timer is started after which time data will be deleted. This is typical of the types of malware attacks that have been increasingly seen over the last 18 months.
What made this ransomware particularly virulent was its utilization of a vulnerability in Windows which enabled its spread to other Windows machines on the network. This vulnerability was originally identified by the U.S. National Security Agency (NSA) and released by a group known as the Shadow Brokers earlier this year. Microsoft released a patch for this vulnerability on March 14, however the infection rates of WannaCry show that this patch was certainly not applied by all.
A security blogger based in the U.K. called MalwareTech identified an effective “kill switch” for this particular virus. By registering the domain name the malware was pinging, it effectively deactivated the virus and stopped its spread.
Impacted Insurance Coverages
Cyber extortion is offered within 74 percent of cyber policies on the market today and clearly represents a potential cause of loss for insurers. Fortunately, ransom payments have totaled only a modest $80,000 so far. However, with a day or so left on the WannaCry timer clocks, it is expected this amount will increase.
Ransom payments are only a small proportion of the total losses that insurers stand to lose. Responding to this event will likely trigger policies that provide coverage for incident response, business interruption (BI) and data and software loss. With several large manufacturers, hospitals and telecoms providers disclosing downtime, the majority of losses for insurers will most likely be represented by BI.
This is not just an issue for cyber insurers. With such a soft property market, several insurers have offered non-damage BI coverage that may trigger. Insurers with Kidnap and Ransom books may also want to look closely at their policies wordings to see whether they are exposed.
Reaction from the Market
For the insurance industry, it is too early to count the cost of this cyber-attack, but it was interesting to get the reaction from close to 200 attendees who joined us at our RMS Cyber Risk Seminar in New York on Monday 16 May, just three days after the event. Unsurprisingly, there was a great deal of discussion and questions about WannaCry. How did it happen? What will the impact be? How can we better protect ourselves? But despite the big questions, the mood was one of cautious optimism, as Reactions reported from the seminar. One important reason given for this is that the vast majority of cyber premiums (around 90 percent) are written in the U.S., whilst the largest impact of this event appeared to be targeted in Europe and Asia.
What is clear from this event though is that the scale of the infections will act as a jolt in the arm to potential cyber insurance purchasers leading to an increased take up of cyber insurance products.
Could It Have Been Worse?
It is still early days but it does appear this could have been a lot worse. Rather than being a true “zero-day” vulnerability, the WannaCry virus utilized a vulnerability that had been patched by Microsoft a full 60 days prior. This gave many companies the opportunity to secure their networks before the attack started. In addition, the presence of a kill switch within the software (in the form of a remote polling web site) allowed security experts to control the spread before too long.
Should this event have used a true zero-day and without the presence of a kill switch, it’s fair to say the scale of this event would have been many orders of magnitude higher.






