A rapidly advancing technology, quantum computing has the potential to solve problems that traditional computers cannot.
Quantum computers can exploit quantum mechanical effects and their properties to accelerate calculations, to usher in a new era of computing that brings both new opportunities – and risks – to many industries, including insurance.
Moody’s RMS has released a white paper in conjunction with Moody’s Quantum Computing team to help raise awareness of quantum computing and its implications for the cyber risk insurance industry.
Our blog provides a quick overview of the paper, to examine what quantum computing is, the potential threat it poses, the current state of quantum technology, and its implications for insurers.
What Is Quantum Computing?
Conventional computers use ‘bits’ to represent information – like a switch that is either on (1) or off (0). Bits are then organized into patterns that a computer can manipulate to perform calculations and solve problems.
Rather than just ones or zeros, quantum computing uses ‘qubits’ which can be in multiple states simultaneously using a property known as superposition. Qubits can also become ‘entangled’ to link the state of one qubit so it is dependent on the state of another.
These properties and a few more allow quantum computers to solve certain problems much faster than conventional computers, such as integer factoring – the process of breaking down a large number into its prime factors.
What Is the Quantum Threat?
This reliance on the inability of conventional computers to quickly solve difficult math problems supports the most common forms of encryption used in cybersecurity and cryptography today, such as asymmetric encryption.
But this encryption could be under attack as it uses integer factoring – a math problem that can be solved by quantum. Quantum computers can solve integer factoring efficiently using Shor’s algorithm, proposed back in 1994. [1]
Integer factoring is the world’s most widely used ‘public-key’ cryptographic algorithm today. It is used in applications such as instant messaging, email, file transfer solutions, credit card point of sale (PoS), and Internet of Things (IoT) device communication.
The Boston Consulting Group estimated that public-key cryptography such as integer factoring secures approximately US$3 trillion of e-commerce annually.
Therefore, large-scale quantum computers will be able to break many of the public-key cryptosystems currently in use, seriously compromising the confidentiality, integrity, and authenticity of digital communications on the Internet and elsewhere.
Any classically encrypted communications that could be wiretapped are also at risk. ‘Harvest Now, Decrypt Later’ or ‘Store Now, Decrypt Later’ tactics are already starting, where data is exfiltrated with the intention of harvesting data now and decrypting later.
Are We There Yet?
The development of quantum is still progressing, and there are many challenges to overcome before the first cryptographically relevant quantum computer could be used for practical applications.
One major challenge is that quantum computers are sensitive to noise, as qubits are fragile and can quickly lose their quantum properties. We are in the noisy intermediate-scale quantum era (NISQ), working hard to build error- and noise-free large-scale quantum computers.
Additionally, quantum computers require specialized hardware making them expensive to build and operate. There are only a limited number of computers available globally, but vendors such as Amazon, Microsoft, and IBM already provide quantum computing easily accessible via the cloud.
Getting insights to monitor this global race to develop increasingly powerful quantum computers is difficult; public sector companies share their findings but progress towards nation-state quantum strategies is largely opaque. [2], [3]).
To get an understanding of the current state of quantum development, expert opinions compiled by EvolutionQ in 2022 (see figure below) show the proportion of respondents who believe that digital quantum computers will be able to break RSA-2048 within 24 hours over various time periods.
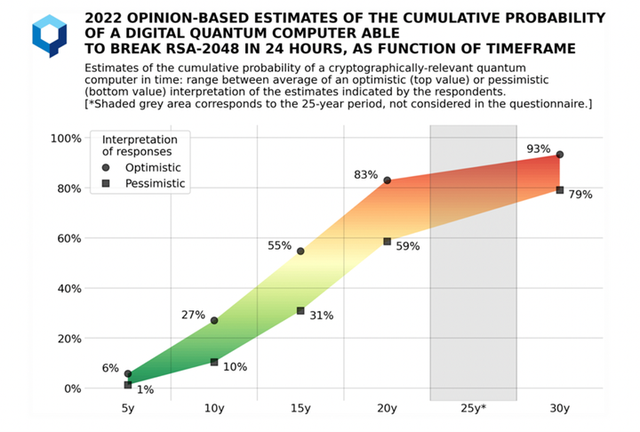
What Is Being Done Globally to Prepare and Mitigate Risks?
We share much more detail on this in the white paper, but currently, there are two main proposed solutions to mitigate quantum threats: Quantum Key Distribution (QKD) based systems and Post-Quantum Cryptography (PQC) standards.
Both are active fields of research, but the main difference is that QKD requires a massive change of infrastructure and communication protocols, while PQC standards would upgrade/change existing cryptographic systems on the current infrastructure to provide resistance to quantum computing attacks.
As seen in the previous EvolutionIQ figure above, the race to develop a post-quantum crypto strategy is on. What timelines are there, and what should the private sector do?
The U.S. National Security Agency issued a 2035 deadline for federal agencies and their vendors to adopt post-quantum algorithms in critical systems related to national security.
The U.S. White House in its National Cybersecurity Strategy has stated that “…the private sector should follow the government's model in preparing its own networks and systems for our post-quantum future.”
Implications for the Insurance Industry
With insurers holding significant cyber exposure, and the market growing strongly, what does all this mean to insurers, and which questions do we have to start asking? Here are five quick takes:
1. Difficulty in Risk Assessment And Modeling: With a highly uncertain timeline around the development and the subsequent adoption of a cryptographically relevant quantum computer, it is difficult for insurers to accurately assess the risk for pricing and capital requirements.
If estimates show a one to six percent probability of quantum computers breaking RSA-2048 in 24 hours in the next five years, this translates into an equivalent 16- to 100-year return period scenario.
Models will also need to adequately reflect the quantum threat on its impact on existing or known cyber threats, and whether there are fundamentally new threats.
For instance, risks around potential ‘store now, decrypt later’ attacks are well understood, however, given quantum’s scale it may have implications on the systemic potential of decryption.
2. Increased Risk Exposure: As quantum computing has the potential to render many of the current encryption standards obsolete, it can make sensitive data and communications vulnerable to attacks. Assessments need to be made on the target industries, data, and potential loss values under a quantum scenario.
3. Change in Coverage Requirements and Insurance Policy Language: What would need to change in terms of data standards, exclusions, or new coverage required?
4. Increased Demand for Cyber Insurance: How can insurers effectively educate businesses about the potential risks posed by quantum computing, and manage increased demand for cyber insurance and new services? Will this affect competition and innovation within the industry?
5. Need for Collaboration and Expertise: Cyber risk insurers must collaborate with experts in the field of quantum computing, cryptography, and cybersecurity, so how can insurers establish effective partnerships, and what role should governments and regulators play?
There is a lot to consider - quantum computers are advancing at a rapid pace, governments are progressing with preparation efforts and cryptographic inventories and strategies, and new standards and protocols are being built.
Download our quantum white paper here, and look out for our series of blogs about post-quantum cryptography and its implication on cyber risk insurance, to start unraveling what this may mean for insurers, assess the many open questions as well as how we can start to measure and quantify the quantum threat.
For more information about what Moody’s is doing in this space, please click here, and please reach out to us if you would like to know more and collaborate.
[1] Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer
https://arxiv.org/abs/quant-ph/9508027
[2] National Quantum Initiative
[3] National quantum strategy - GOV.UK (www.gov.uk)








